The best backup and recovery enhanced with essential endpoint protection capabilities and security management toolkit for centralized administration and monitoring.
Acronis Active Protection technology
Protect your clients from modern cyberthreats. Our award-winning anti-ransomware technology with built-in automatic recovery from ransomware is now enhanced with AI-based static and behavior anti-malware analysis focused on zero-day threats.
#CyberFit Score
Increase your clients’ security posture by addressing the gaps in their IT environment. Acronis #CyberFit Score assesses and scores a set of security metrics to identify gaps and then provides recommendations for how you can improve their overall security.
Vulnerability assessments
Identify and close the security gaps in your clients systems. You can scan client machines for vulnerabilities to ensure that all applications and operating systems are up-to-date and can’t be exploited by cybercriminals.
- Protection for remote workers – Minimize the rising risk of cyberattacks for remote workers with multiple protection capabilities – including prioritized patching and protection for mission-critical telecommute apps (Zoom, WebEx, MS Teams, Slack, Skype, TeamViewer), remote device wipe, and secure desktop remote connectivity.
- Multiple backup types – Back up disks/volumes (with all information required for the operating system to boot), individual files or folders, system states (for Microsoft Windows systems), or ESXi configurations.
- Flexible backup storage options – Comply with the requirements of different clients with flexible storage options. Back up to Acronis-hosted cloud storage, public clouds such as Google Cloud Storage or Microsoft Azure, your own cloud storage, or local networked storage.
- Device and port control – Strengthen data security and prevent leakage of sensitive information via local channels with granular, context-aware controls over user access to locally connected devices and ports, and data operations related to them – even for virtulized sessions.
- Clipboard control – Prevent data leakage in its earliest stage by controlling data transfers between application and documents. Allow or block user access to objects of different data types copied to the clipboard, even for redirected BYOD devices in virtualized sessions.
- Device control: support of encrypted removable media and screenshot capture access – Eliminate the risk of data leaks with encrypted removable media and screenshot capture control. This enables users to keep sensitive information within their organization – should a removable device get in the wrong hands or prevent screenshots from being copied to the clipboard. Keeping your clients’ sensitive data safe and secure.
- Acronis Instant Restore – Cut RTOs to as little as 15 seconds with a built-in capability to restore a system by booting it as a virtual machine directly from the backup, without moving any data.
- Acronis Universal Restore – Reduce the time spent on recovery tasks. Acronis Universal Restore makes recovery to dissimilar hardware faster by detecting the machine type and auto-installing appropriate drivers for the hardware.
- Google Workspace data protection – Safeguard client data stored in Gmail, Drive (including Team Drives), Contacts, and Calendar by backing it up to ensure fast, reliable recovery.
- Complete Microsoft 365 protection – Protect data in Microsoft Exchange Online, OneDrive for Business, Microsoft Teams and SharePoint Online with comprehensive cloud-to-cloud backup and restore.
- Backup encryption – Maintain regulatory compliance and strengthen data protection by securing your backups with AES-256 data encryption for data in transit and at rest, so only you can access the data.
- Deduplication – Minimize storage requirements by detecting data repetition in backups and not storing identical data more than once. Deduplication also reduces network load as duplicate data is not even transferred over the network to the backup storage.
- Report scheduling – Increase visibility into information security and simplify IT security auditing with capabilities for sending scheduled reports to listed recipients in a desired format and language.
- Multi-tenant enablement of services, packs, offering items – Save time and money when you need to add new services, billing modes, advanced packs, or offering items across multiple clients.
Monitoring and reporting
Simplified, at-a-glance reporting helps streamline operations while giving your technicians the insight they need to support your clients. Customize your dashboard’s widgets to view a wide range of reports – enabling you to quickly identify and remediate problems.
Centralized protection plans and group management
Ease administrative efforts with the ability to group manage multiple workloads and centralized protection plans that include all security configurations that can be applied to multiple endpoints across your client’s organization.
- Auto discovery and remote installation – Simplify the onboarding process by installing multiple agents at once – in the cloud and on-premises. With network-based and Active Directory-based discovery, your technicians can easily install and apply protection plans remotely – helping to keep your clients safe.
- Predefined protection plans – Protect your clients’ remote and office workers quickly and easily by choosing one of three preconfigured protection plans. These options save you time while ensuring you that your clients’ workloads and environments are protected.
- Remote desktop assistance – Enable secure, off-site access to machines to ease remote work for users or provide technical assistance to clients with built-in remote desktop capabilities.
- Hardware inventory collection – Save time and effort with an up-to-date hardware inventory. Discover all hardware assets with automatic and on-demand scans. Create hardware inventory reports, browse and filter records by multiple criteria and auto-delete them once a machine or tenant is removed.
Secure file sync and share
Ensure client productivity by offering convenient, secure file sync and share capabilities. Users can securely create, edit, and share content using their own devices with pay-as-you-go pricing.
Notarization
Give clients proof of their data’s authenticity by giving them the ability to notarize any type of file, which generates a certificate with immutable, publicly verifiable proof of the file’s timestamp, integrity, and authenticity. Based on a pay-as-you-go pricing model.
Multi-tier and multi-tenant management
Count on optimal administrative efficiency: create client or partner accounts in seconds, customize unique offerings, and manage quotas, features and administrative privileges using vertical grouping.
- Electronic signing – Strengthen process compliance by allowing clients and their third parties to e-sign documents with publicly verifiable proof of the timestamp and authenticity of the signature. Based on pay-as-you-go pricing.
- Test failover in isolated network environments – Verify the integrity and efficiency of disaster recovery plans by executing them via the web console in an isolated network environment, without disrupting other processes.
- Point-to-site VPN connection – Enable clients to quickly and easily access files from the local site or the cloud. With the Business VPN feature, clients on DR-enabled tenants can establish a secure connection to the corporate network with their personal devices so they can access the data they need.
- Firewall policies management – Easily manage firewall policies on your clients’ behalf for their disaster recovery servers through the Acronis Cyber Protect Cloud console. This enables you to simplify the support process and manage outbound and inbound firewall policies.
- Straightforward pay-as-you-go pricing – Meet the dynamic needs of your clients with a 100% pay-per-use licensing model and free functionalities.
- Integration with PSA and RMM systems – Deliver services instantly using native integrations with ConnectWise (Automate, Manage, Control), Atera, Autotask, Kaseya, cPanel, HostBill, CloudBlue, Plesk, and WHMCS.
- Integration with custom systems – Assimilate systems by leveraging a powerful RESTful management API or enable integration via the Acronis Cyber Backup Cloud Application Packaging Standard (APS).
- Ransomware-proof backups – Ensure backups cannot be encrypted or deleted by a ransomware attack or malicious users through immutable storage, enabling you to recover quickly to the most recent clean state.
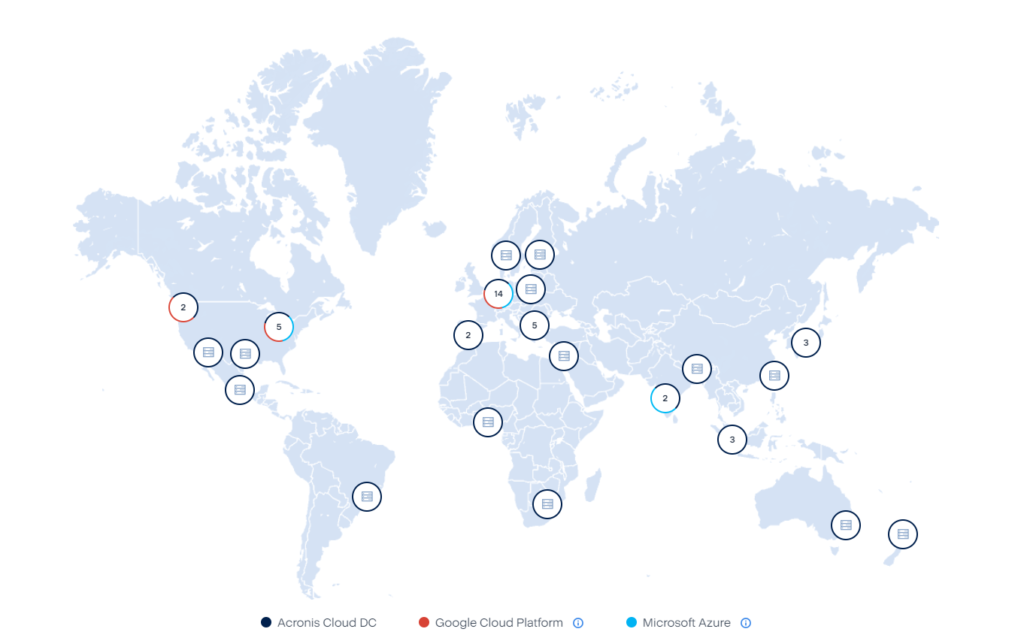
Acronis Datacenters across the Globe.